This is a sample Django app to authenticate with GitHub as a third-party OAuth2 provider.
This app is deployed on AWS running SSL here. This app contains a secret page whose secret content can only be viewed after authenticating with GitHub.
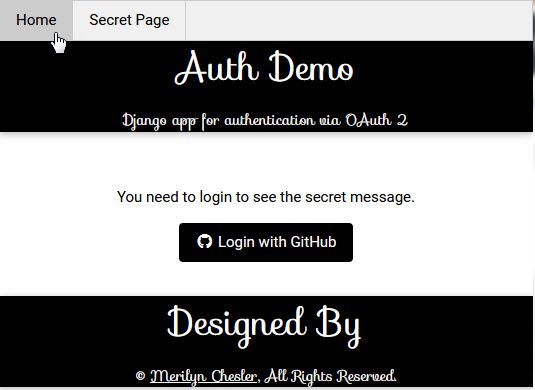
Before authentication, the secret page looks like this:
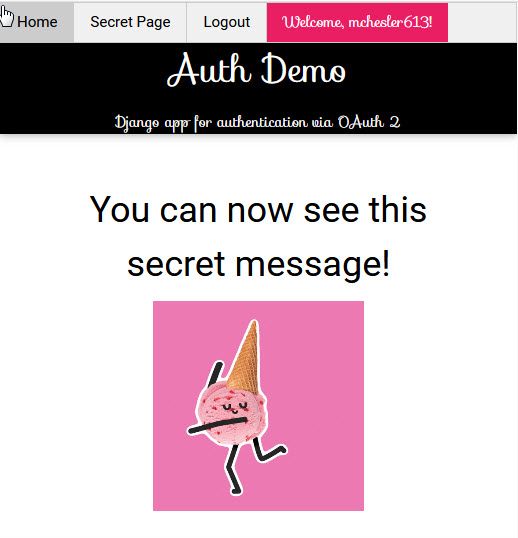
After authentication:
This app uses the following Python packages
- python-dotenv, to store sensitive information
- oauthlib, to integrate with third-party OAuth2 providers, such as GitHub
- requests, to send HTTP GET and POST requests
Other requirements include:
- a GitHub account to login
- a GitHub OAuth developer account to generic credentials such as
client idandclient secret. - an SSL connection to implement a client callback with a URL endpoint that receives communication back from GitHub's OAuth service.
- I wanted to understand and learn how to integrate with a third-party OAuth2 provider by writing some code myself, instead of plugging in a third-party Django app
- With oauthlib, I am able to write a client service that completes the OAuth2 flow between the client and provider, which requires these steps:
- request authorization from GitHub at an authorized GitHub URL with
client idandstateinformation and expecting acodeback - receive a
codeback from GitHub with the priorstateinformation at the client's callback URL - fetch a token from GitHub's token URL passing
client secretandcodeas arguments - retrieve the authorized user profile data from GitHub as
JSONdata - create a Django
Useraccount or reuse an existing authorizedUseraccount - login to Django with
Useraccount - proceed with Django app logic based on
Userprivileges
- request authorization from GitHub at an authorized GitHub URL with
To learn more about GitHub's OAuth2 flow, refer to this doc.
I wrote a supporting article for this project here. If you found any bugs, or would like me to improve this article, please don't hesitate to contact me. Thanks.